Netutils dll Virus Removal
S0373 Astaroth Astaroth uses a fromCharCode() deobfuscation method to avoid explicitly writing execution commands and to hide its code. S1028 Action RAT Action RAT can use Base64 to decode actor-controlled C2 server communications. ID Name Description S0469 ABK ABK has the ability to decrypt AES encrypted payloads.
DLL virus infects the memory space and doesn’t let other programs to use the memory space. Though the DLL virus attacks the DLL files which are only a part of the software download msvcp100_dll here program, the user should replace the whole software instead of only the infected DLL files. Actually DLLs are files which contain the settings and give the computer instructions about some specific programs.
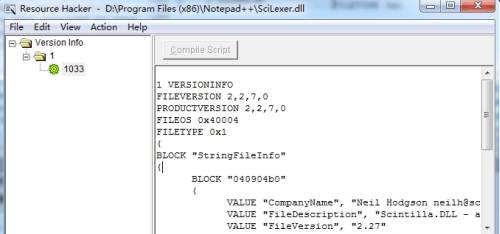
Checking for a missing DLL file (Windows
Let us know in the comments below if you face any other sens.dll issues. Then Search for sens.dll or the software name Microsoft Windows Operating System in the search bar or try out the developer name Microsoft Windows Operating System. All you know is that if it is flagged by an anti-virus program then it is all most certainly harmful.
RAW formats – It is not recommended to remove all metadata from RAW images because this will likely remove some proprietary information that is necessary for proper rendering of the image. PNG – Only XMP, EXIF, ICC_Profile and native PNG textual data chunks are removed. Even though ExifTool does some validation of the information written, it is still possible to write illegal values which may cause problems when reading the images with other software. So take care to validate the information you are writing. Alternatively, information may be written to a specific group only, bypassing these priorities, by providing a group name for the tag.
- It is automatically generated when you first install Orchestrator.
- Unfortunately I’ve tried 3 times to delete the virus with Sophos, and it keeps reapearing after Sophos tries to delete it, which requires a full system scan and a restart of the system.
- If the Array does exist though, then we return the value they asked for “m_piTradeYieldModifier” which would be the variable stored in the “i’th” location of this array.
In safe mode, using unlocker caused the locking processes to crash, but I WAS able to delete the troublesome DLL before Windows restarted. In this case, the WerFault.exe process spawned to report an error in Microsoft.VsHub.Server.HttpHostx64.exe, the process whose DLL we hijacked. The crash happened because we tried to write a file into the System32 folder in our malicious DLL. Figure 3For all of you developers, you’ve probably seen this type of error at least once. This error is invoked by the WerFault.exe process.
LogiLDA.dll: How to Fix It on Windows
For instance, the .NET assembly does not contain the names of local variables. The program can automatically assign local names in accordance with their types (what Dis# really does), but it still too differentiates from the original source. Assemblies that decrypt themselves at runtime can be debugged, dnSpy will use the in-memory image. You can also force dnSpy to always use in-memory images instead of disk files.
If Process Explorer is in DLL mode you’ll see the DLLs and memory-mapped files that the process has loaded. A Windows DLL file is a library of machine code meant to be loaded by a piece of software. An experienced developer may be able to decompile the library into x86 assembly language.